CYBER SECURITY SOLUTIONS FOR BUSINESSES
CYBER SECURITY SOLUTIONS FOR BUSINESSES
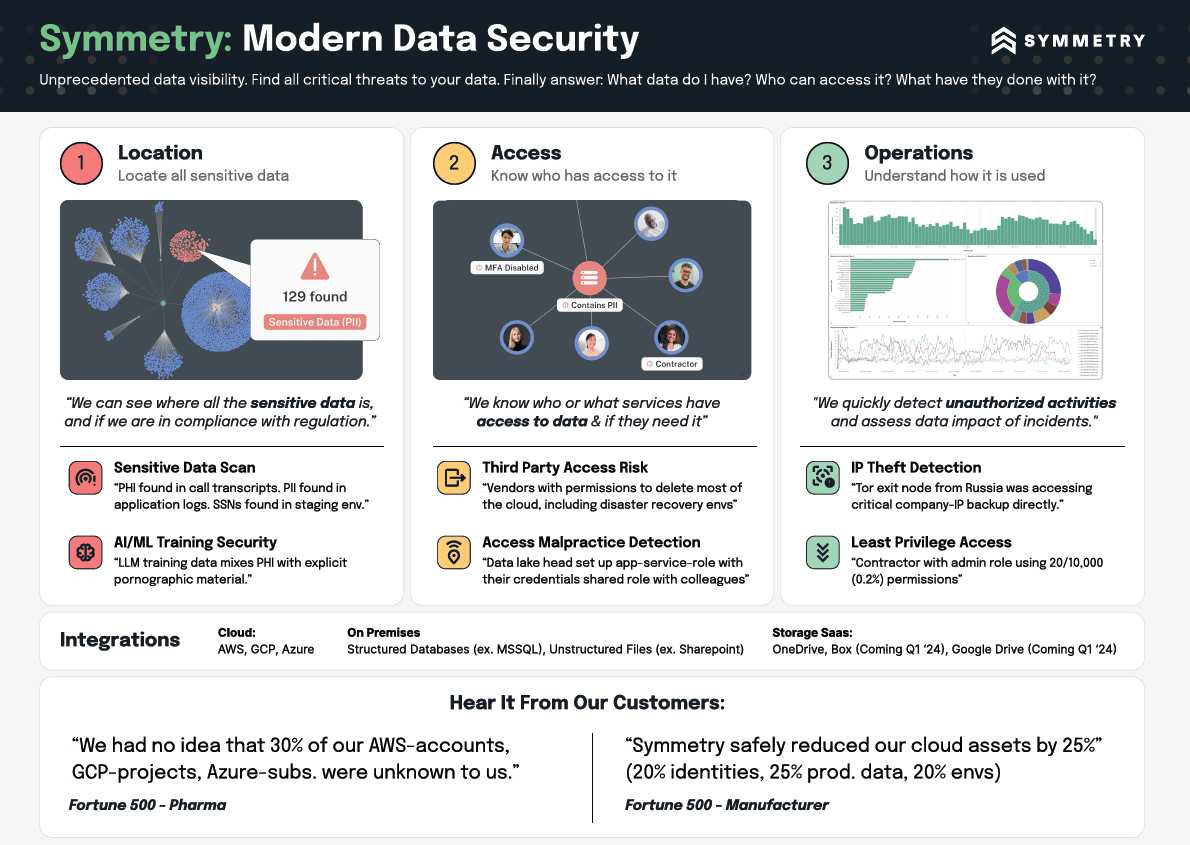
- Visualizing and Securing Data and Data Flow Across Environments
- Manage Compliance and Privacy at the Data Object Level
- Reducing the Data Blast Radius from Insider Threats, Vendors, and Third Parties
- Anomalous Data Behavior Monitoring and Alerting
- Leading with Effective Data Breach Investigation and Response